PEUNION Crypter 2024
PEUNION Crypter 2024 CRYPTER, BINDER & DOWNLOADER
PEunion encrypts executables, which are decrypted at runtime and executed in-memory.
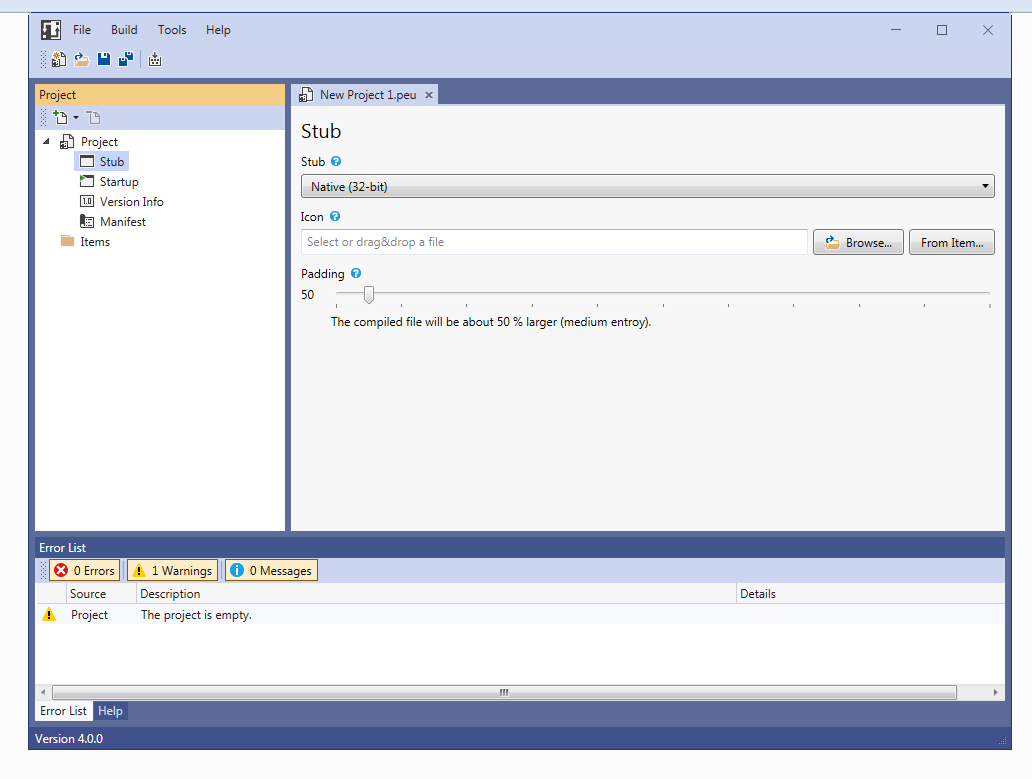
STUB
Two stubs are available to choose from, both of which work in a similar way.Native: Written in assembly (FASM)
.NET: Written in C#
KEY FEATURE of PEUNION Crypter 2024
Emulator detection
Low-entropy packing scheme
Two-layer execution architecture
Code obfuscation
File compression
Binder (combine multiple files)
Downloader
RunPE (process hollowing)
In-memory invocation of .NET executables
Drop files to disk
Melt (self-deleting stub)
EOF support
Specify icon, version information & manifest
Well-designed UI
Commandline compiler
Multiple files can be compiled into the stub. A file can either be embedded within the compiled executable,
or the stub downloads the file at runtime.Typically, an executable is decrypted and executed in-memory by
the stub. If the executable is a native PE file, RunPE (process hollowing) is used. For .NET executables,
the .NET stub uses Invoke. Legitimate files with no known signatures can be written to the disk.IMPLEMENTATION & EXECUTION FLOW
Obfuscation and evasive features are fundamental to the design of PEunion and do not need further configuration.
The exact implementation is fine tuned to decrease detection and is subject to change in future releases.This graph
illustrates the execution flow of the native stub decrypting and executing a PE file. The .NET stub works similarly.
The fundamental concept is that the stub only contains code to detect emulators and to decrypt and pass execution to the next layer.
The second stage is position independent shellcode that retrieves function pointers from the PEB and handles the payload.
To mitigate AV detections, only the stub requires adjustments. Stage 2 contains all the “suspicious” code that is not readable at
scantime and not decrypted, if an emulator is detected.The shellcode is encrypted using a proprietary 4-byte XOR stream cipher.
To decrease entropy, the encrypted shellcode is intermingled with null-bytes at randomized offsets. Because the resulting data has
no repeating patterns, it is impossible to identify this particular encoding and infer YARA rules from it. Hence, AV detection is
limited to the stub
Download Link



















