Just one message leads to the theft of companies' confidential information.
Researchers at Menlo Security have discovered a new phishing campaign targeting the Microsoft 365 accounts of key executives at US organizations. As part of the campaign, cybercriminals are abusing Open Redirects from the job search site Indeed.
The attacker uses the EvilProxy phishing tool, which can collect session cookies, which allows you to bypass Multi-Factor Authentication (MFA) mechanisms.
Menlo Security says the phishing campaign is targeting executives and senior-level employees from a variety of industries, including electronics manufacturing, banking and finance, real estate, insurance and property management.
Open Redirect is a type of vulnerability where a web application allows a user to be redirected to arbitrary external URLs without proper validation. This means that an attacker can create a malicious link that redirects the user to fake or dangerous websites. Because the link comes from a trusted source, it can bypass email security measures or rank higher in search results without raising suspicion.
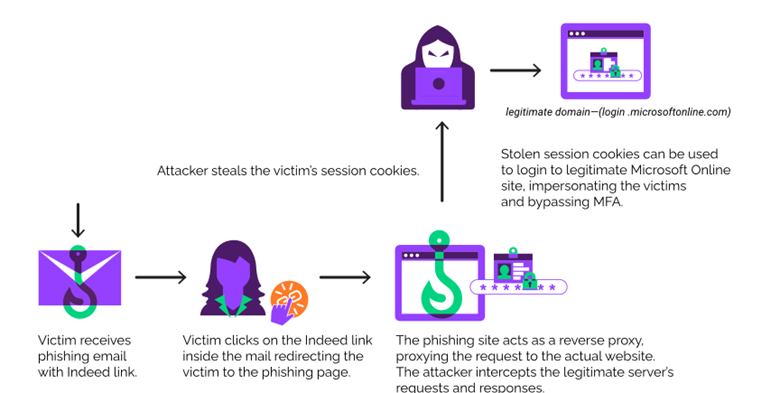
In the detected campaign, attackers use an open redirect to indeed.com, an American job search site. Targets receive emails with a link to indeed.com that appears legitimate. When accessed, the URL redirects the user to a phishing site that acts as a reverse proxy for the Microsoft login page.
EvilProxy is a Phishing-as-a-Service (PaaS) platform that uses reverse proxies to facilitate communication and transfer of user data between a target and a genuine online service (in this case, Microsoft).
When a user accesses their account through a phishing server that imitates a login page, the attacker can capture the victim's cookies. Since the victim has already completed the required MFA steps during login, the stolen cookies give the cybercriminal full access to the victim's account.
The uncovered phishing campaign highlights the growing use of sophisticated techniques by cybercriminals to bypass security systems and target key executives in leading industries. Effectively exploiting PaaS and website vulnerabilities to redirect users to fake login pages threatens not only individual security, but also corporate security on a broader level.
Attackers who gain access to the accounts of senior management can gain access to confidential information, which can lead to significant financial losses and damage to the reputation of companies. The attack highlights the need to strengthen cybersecurity measures and train staff to be aware of phishing threats to minimize risks and ensure strong protection against such attacks.
__________________
Researchers at Menlo Security have discovered a new phishing campaign targeting the Microsoft 365 accounts of key executives at US organizations. As part of the campaign, cybercriminals are abusing Open Redirects from the job search site Indeed.
The attacker uses the EvilProxy phishing tool, which can collect session cookies, which allows you to bypass Multi-Factor Authentication (MFA) mechanisms.
Menlo Security says the phishing campaign is targeting executives and senior-level employees from a variety of industries, including electronics manufacturing, banking and finance, real estate, insurance and property management.
Open Redirect is a type of vulnerability where a web application allows a user to be redirected to arbitrary external URLs without proper validation. This means that an attacker can create a malicious link that redirects the user to fake or dangerous websites. Because the link comes from a trusted source, it can bypass email security measures or rank higher in search results without raising suspicion.

| Attack chain |
EvilProxy is a Phishing-as-a-Service (PaaS) platform that uses reverse proxies to facilitate communication and transfer of user data between a target and a genuine online service (in this case, Microsoft).
When a user accesses their account through a phishing server that imitates a login page, the attacker can capture the victim's cookies. Since the victim has already completed the required MFA steps during login, the stolen cookies give the cybercriminal full access to the victim's account.
The uncovered phishing campaign highlights the growing use of sophisticated techniques by cybercriminals to bypass security systems and target key executives in leading industries. Effectively exploiting PaaS and website vulnerabilities to redirect users to fake login pages threatens not only individual security, but also corporate security on a broader level.
Attackers who gain access to the accounts of senior management can gain access to confidential information, which can lead to significant financial losses and damage to the reputation of companies. The attack highlights the need to strengthen cybersecurity measures and train staff to be aware of phishing threats to minimize risks and ensure strong protection against such attacks.
__________________


















